Projects Background
Information is everything for companies nowadays, and Fortifier makes data more reliable and trustworthy for IIoT (Industrial Internet of Things). Combining cutting-edge and Cloud technologies, we built a secure tool for protecting the organization from external threats, data losses, and other unfortunate events.
Our Clients Background
Our customer specializes in Industrial IoT. Working smarter, not harder—it is the main motto pushing their business forward. The solution had to be focused mainly on small and middle manufacturers so that not only big enterprises could have access to the latest innovations.
Smart Factory is a revolutionary approach to organizing the work of today’s factories. IT solutions should be an integral part of the business progress fitting restrictive and complex environments. The idea of the system was based on the basic—but very important—requirement: all tools taking part in the production must be safe and well-protected.
Client's Challenges
The speed of industrial progress is overwhelming, and one of the recent developments in this field is the appearance of connected devices. But much haste can make waste, so the digitization era has brought three significant challenges along with the numerous benefits:
1. Vulnerable security. A huge number of devices creates a fragile network within a factory. It’s very hard to look after each component of the system, so it becomes an easy target for cyber attacks.
2. Operational improvements. Operations were and still are the core of any manufacturing process. New technologies should become a part of this process at its every stage.
3. Complex management. Lots of devices lead to another problem—it’s hard to cope with each of them. It is necessary to keep an eye on every device and data flows between them, i.e. the monitoring should be thorough.


Our Solutions
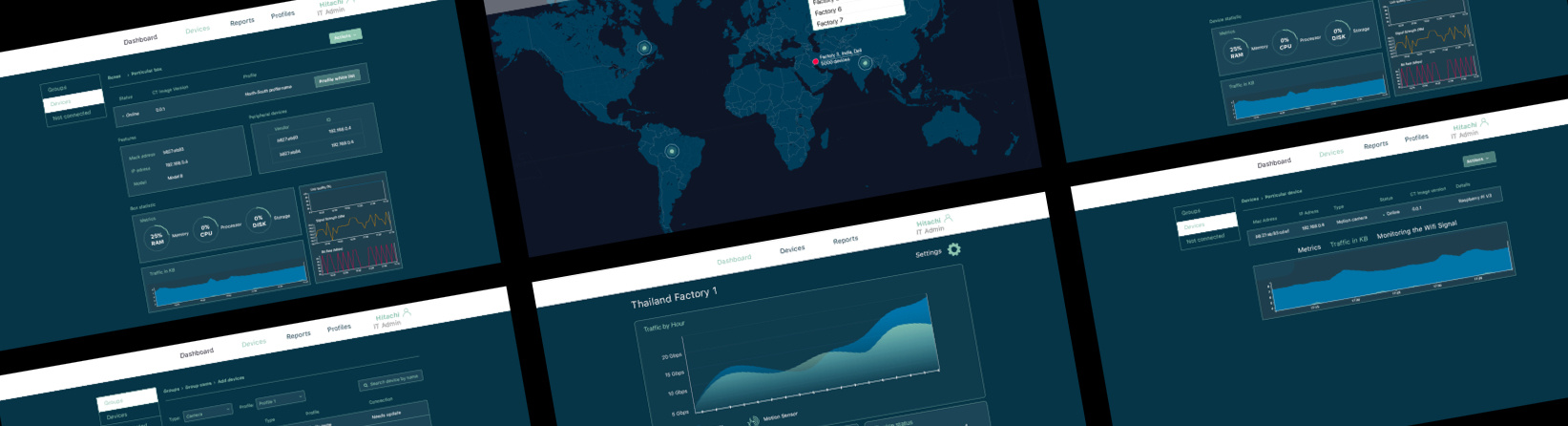
The result of our collaboration with the company founders is The New IIoT Technology. It allows building a solid network of devices within factories no matter how big they are. All of the devices are thoroughly monitored, so managers wouldn't miss any security or operational bottlenecks. Our solution keeps an eye on both the device and data it transfers, so, the whole system is working like a clock.
The flow of solution includes two directions: monitoring devices and monitoring infrastructure.
Monitoring Devices
The special agent is installed on the specific device to monitor it. The things checked by the system are:
- Hardware
- The system’s software
- Every app installed on the device
- The device’s connectivity.
From now on, the device is checked constantly, so any behavior changes won’t pass unnoticed. The solution assigns a trust score to each device based on the results of the monitoring. Thanks to the real-time data processing, any malfunction is detected immediately.

Monitoring Infrastructure
When every device is monitored, the whole network is in the palm of your hand. Traffic and data streams are another vital part of the production process. The system allows collecting metrics of both wired and wireless networks.
Security is the main selling point of the solution, so we focused heavily on implementing it. All data transfers (including during device onboarding) are made using a secure protocol. To ensure data reliability, the system adds a label with encrypted authenticity proof (including geolocation data) to every piece of data transferred in the system. Moreover, all the data is stored on an original blockchain to ensure its safety.
Ultimately, we have a system that makes devices and transferred data secure and reliable, so they can work for the company’s benefit.
Value Delivered By Fortifier
Fortifier’s team did its best to create a fast, clear, and simple system. We focused on the following points:
The online installation process is easy to understand, the flow is intuitive, and the setup is fast
Convenient, factory-level dashboard for admins with device profiles and detailed, visualized reports
Blockchain implemented as the core technology of the Trust-as-a-Service concept
Easy scaling and device expansion
Support of several third-party hardware providers
Servers and processors provided by Intel technologies
Technologies Used
Here's the technology stack we chose to implement the solution: